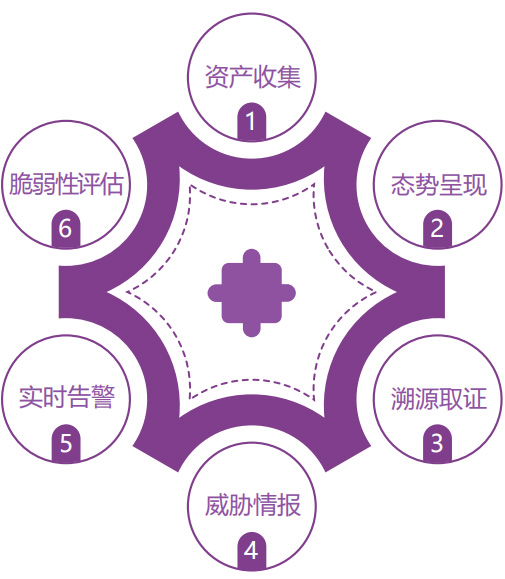
| 01, through the active and passive asset detection methods, real-time accurate continuous monitoring of asset changes, automatic identification of network equipment, host, security equipment, operating system, database, web application and other assets.
02. Various security data are collected and classified, including the following categories: asset situation, vulnerability situation, network threat situation, intrusion attack situation, Web attack situation, vulnerability attack situation, lost host situation, network traffic situation, zombie Trojan horse situation, ransomware situation.
03. Store and extract metadata of the original message of the current threat event, implement traffic analysis, data drilling and threat tracing functions, automatically store traffic files related to threat behavior, and provide basis for system diagnosis and maintenance.
04. Support the linkage with the third party security agencies or manufacturers, form the sharing and sharing of threat intelligence, and improve the ability to detect security threats.
05, focus on showing the system found major network security risks, intrusion attacks, security vulnerabilities, malicious programs spread events, sudden network security events, etc., through email or SMS timely warning.
06. Vulnerability system vulnerability library covers mainstream operating system, database, web middleware, network equipment, security equipment, etc. Asset evaluation is carried out from two dimensions of asset vulnerability and vulnerability impact.
|